Understanding the challenges of fraud and strategically combatting the complex issues fraud presents are urgent imperatives for a business to succeed in today’s digital era. With nine out of ten consumers reporting that they’ve used some form of digital payment within the last year, and engagement rates up 6.5% across age groups and income brackets, the volume of digital activities and transactions are on the rise – and effective fraud prevention measures have never been more critical to safeguard a business’s bottom line. Traditional anti-fraud methods, like device checks, two-factor authentication (2FA), biometrics and security questions, are outdated against emerging innovative technologies that are compelling new forms of sophisticated fraud.
Historically, companies have resorted to a patchwork of point solutions and variegated tools across a fraud-fighting tech stack, leading to fragmented data and operational inefficiencies from switching from one solution to the subsequent and obfuscated risk views. The global market for fraud detection and prevention solutions is expected to reach over $50 billion this year.
While certain platforms offer more comprehensive solutions, some take on the role of orchestrator, overly relying on third-party data that can limit access to real-time, direct-to-source intelligence and exacerbate the inflation of anti-fraud measures. Additionally, the rise of AI and machine learning are introducing newly advanced, sometimes opaque, fraud detection systems based on blackbox machine learning, rendering teams without clear insights or customization options to tailor solutions to their business use case and best workflows. As the battle against fraud intensifies, understanding the fraud solution landscape and how to move forward best to adapt to evolving conditions is essential for safeguarding businesses.
Harness the power of AI and machine learning to outsmart fraudsters and preserve your competitive edge.
Speak with an Expert
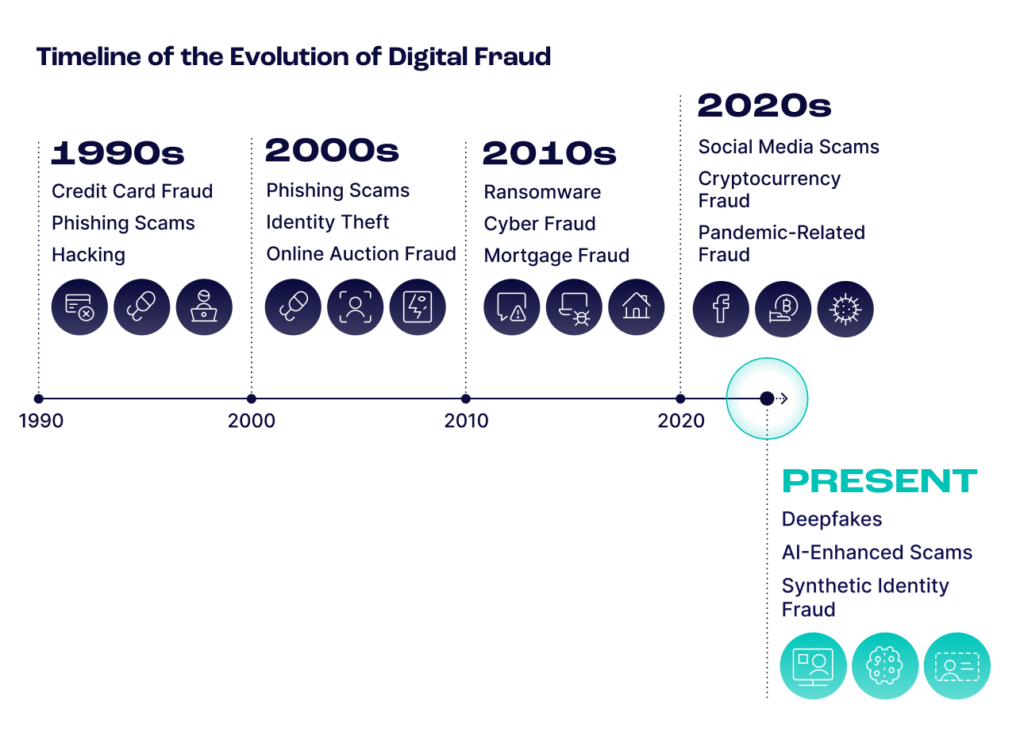
How Fraud is Evolving
Today, we see bad behaviors amplified in scale and speed. As cybercriminals adapt to technological advancements, more than traditional methods is needed.
Dismantling 2FA
Take 2FA, for example. Brute force attacks, once deemed laborious and impractical, have evolved alongside computing power and algorithmic sophistication, enabling cybercriminals and fraudsters to employ automated tools to systematically test countless usernames and passwords until they breach an account, rendering even the most complex combinations vulnerable to exploitation. Add in social engineering to circumvent the safeguards put in place by 2FA – whether through deceptive phone calls, fraudulent websites or other social engineering tactics that prey on the inherent vulnerabilities of human cognition – and the outcome results in unsuspecting users divulging sensitive data that allows fraudsters to bypass 2FA altogether.
Making Device Checks Moot
Another anti-fraud security protocol, device checks, refers to the process of verifying the identity and integrity of a device that is attempting to access a system or service. Device checks have proliferated alongside the rise of mobile devices, and with them has come a myriad of vulnerabilities, exploited by cybercriminals through techniques such as SIM swaps and mobile malware attacks.
SIM swaps involve the unauthorized transfer of a user’s phone number to a different SIM card, typically controlled by the attacker. This enables the fraudster to intercept authentication messages, bypassing security measures that rely on SMS verification. Other types of mobile malware attacks facilitated through malicious apps or software vulnerabilities can compromise the integrity of devices, providing attackers with unauthorized access to sensitive information.
With inherent portability and connectivity, mobile devices are prime targets for exploitation, and contemporary cybercriminals are leveraging these characteristics to perpetrate more fraud than ever before, including phishing scams, malicious apps and social engineering tactics explicitly tailored for mobile platforms. The reliance on mobile devices for authentication and real-time transactional purposes has created a lucrative landscape for attackers seeking to exploit vulnerabilities in cellular networks and device security.
Outmoded Security Questions
Once a standard method for verifying user identity and recovering account access, security questions have become increasingly vulnerable in the face of evolving fraud tactics. These questions prompt users to provide personal information, such as their mother’s maiden or first pet’s name. However, with the widespread availability of personal information on social media and other online platforms, security questions have become more accessible for fraudsters to bypass.
Social media mining is another tactic in which bad actors systematically extract personal information from social media profiles and other online sources to leverage in targeted attacks, accurately answer security questions and gain unauthorized access to accounts.
Another way that this outdated security standard has become obsolete is through the proliferation of data breaches. Large-scale breaches expose vast amounts of personal information and provide fraudsters with ready-made answers to the most common security questions. This means that even individuals who diligently safeguard their personal information may find themselves vulnerable if their data has been compromised in a breach.
Challenges to Biometrics
When biometric authentication burst into the technology scene from 2000 to 2010, industries witnessed widespread integration into consumer devices, particularly fingerprint and facial recognition. What was heralded as high security due to a reliance on unique biological characteristics is now facing challenges from emerging fraud technologies such as spoofing and deepfakes.
Spoofing involves replicating or falsifying biometric data to deceive authentication systems. For instance, fraudsters can create synthetic fingerprints or 3D facial models to mimic legitimate biometric traits and trick sensors into granting unauthorized access. This technique undermines the integrity of biometric authentication, as systems cannot distinguish between genuine biometric data and spoofed replicas.
The rise of deepfake technology presents another significant threat to biometric authentication systems. Deepfakes utilize artificial intelligence (AI) algorithms to create highly realistic synthetic media, including videos or audio recordings, that convincingly depict individuals saying or doing things they never did. In biometric authentication, deepfakes can generate lifelike replicas of an individual’s facial features or voice, which can then be used to bypass biometric security measures.
In response to these threats, ongoing research and development efforts are focused on enhancing the robustness of biometric authentication systems against spoofing and deepfakes. This includes integrating liveness detection mechanisms that verify the presence of a live person during biometric capture and utilizing multi-modal biometrics that combine multiple biometric modalities for enhanced security. Additionally, ongoing vigilance and awareness are essential to staying ahead of evolving fraud tactics and ensuring the continued effectiveness of biometric authentication in the face of emerging threats.
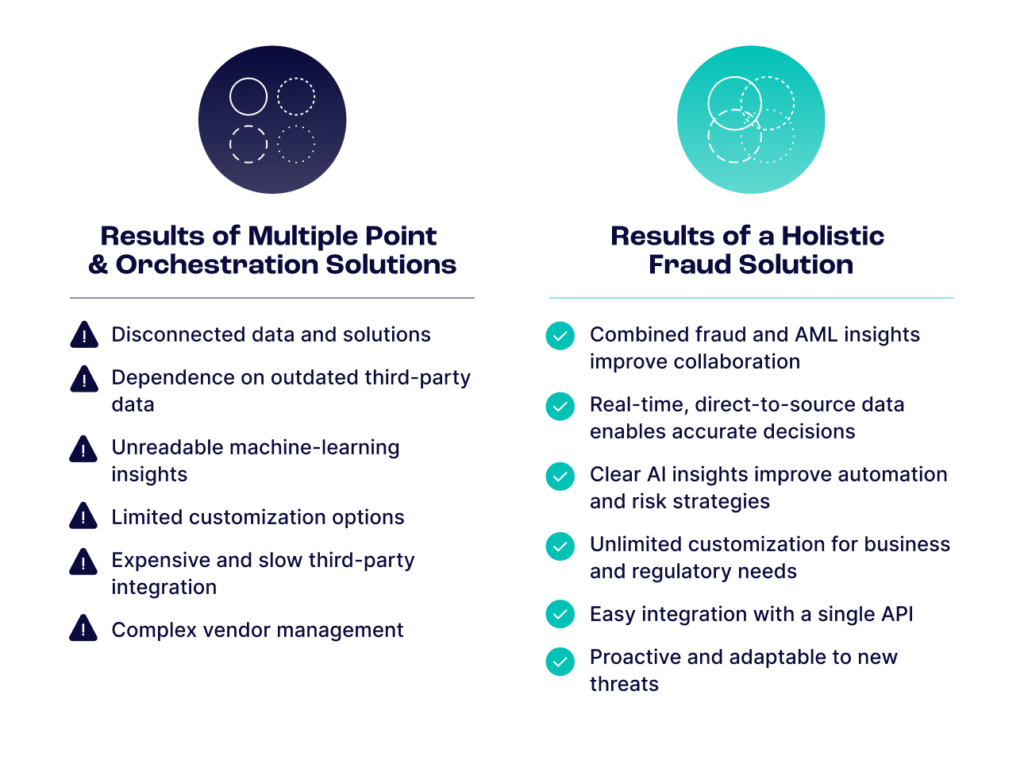
Where Solutions Fall Short
A reliance on point solutions results in a disjointed approach that fails to provide a holistic view of fraudulent activities. Instead of implementing a comprehensive strategy, businesses often resort to piecemeal tech stacks to address each specific aspect of fraud detection – and frequently, the various puzzle pieces employ outdated technologies that make management a nightmare.
With data scattered across different systems, it’s a significant challenge to correlate information, connect the dots and identify overarching patterns of bad behavior. This decentralized approach causes businesses to overlook crucial fraud indicators and struggle to respond effectively to emerging threats due to the lack of visibility and coordination among disparate fraud prevention tools. While some platforms offer comprehensive fraud prevention capabilities, they may heavily rely on third-party data sources, including legacy datasets, to inform their decision-making processes. Certain third-party data providers serve valuable insights, but they often come with limitations, such as latency and incomplete coverage, mainly when dealing with rapidly evolving fraud tactics.
Others partner with orchestrators – entities that rely on third-party solutions and integrate them into their platforms. This approach offers convenience but comes with drawbacks as multiple solutions extend timelines, lead to delays in implementation, and encourage a disjointed experience characterized by varying user interfaces and third-party markups. As a result, businesses may be disadvantaged and need help accessing the timely and accurate intelligence required to detect and mitigate fraudulent activities in real time.
Don’t let fraud drain your resources. Take proactive steps to ensure business continuity.
Speak with an Expert
The Balancing Act Between Fraud Prevention and Business Success
To successfully navigate the fraud solution landscape, companies must embrace integrated fraud prevention platforms that offer consolidated data management and access to real-time intelligence directly from credible sources. They must also leverage AI-driven decision-making capabilities to refine and automate efficiencies while keeping pace with shifting threat vectors. This includes the ability to customize rules based on changing business needs and ensuring a proactive and adaptable approach to fraud prevention and money laundering detection. The solutions that win are those that stop fraud at the earliest point possible across the customer journey, resulting in cleaner ecosystems, happier customers and more bottom line in the bank.