From the SEON Command Center: flexible analysis Edition
Risk Tools for Flexible Analysis
Execute risk-based workflows at scale, and with ease, through custom AML screening, regulatory rule organization and clear insight into alert trends.
Adapt AML Screening Profiles & Rules to Your Risk-Based Policy
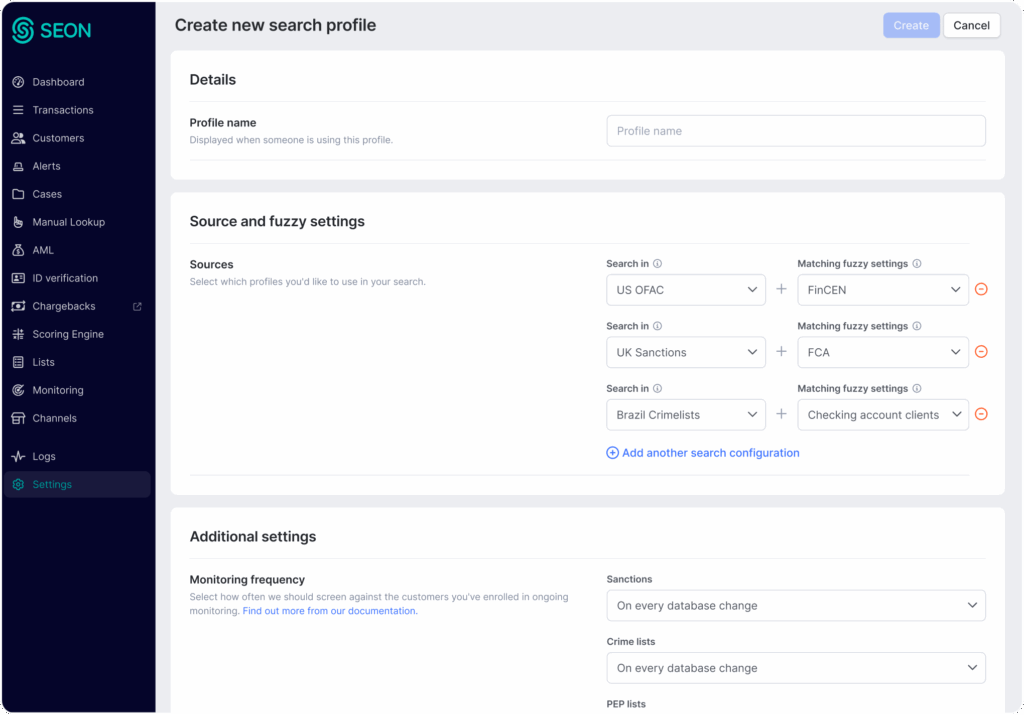
AML SEARCH PROFILES
Screen Customers to Your Exact Requirements
Build custom AML search profiles for customer and payment screening by pairing specific data sources with configurable fuzzy logic settings per list or source type, without code.
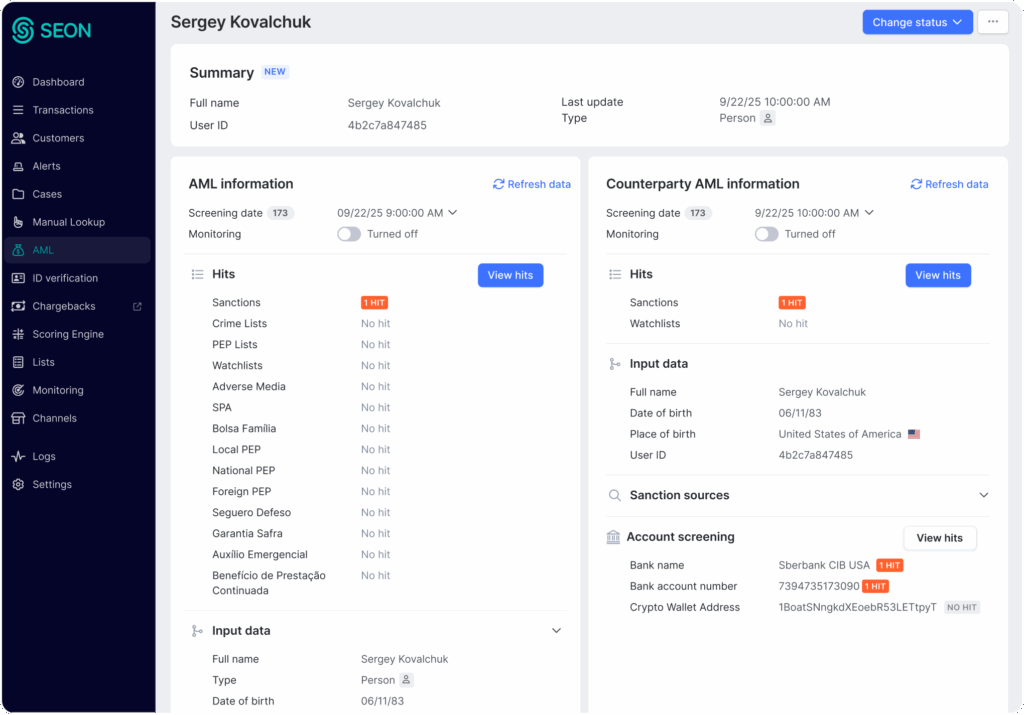
PAYMENT SCREENING
Check Risky Banking Identifiers and Crypto Wallets in Real Time
Uncover and block risky transactions before they’re processed. Identify high-risk institutions and flagged crypto wallets to safeguard your payment flows with precision and control.
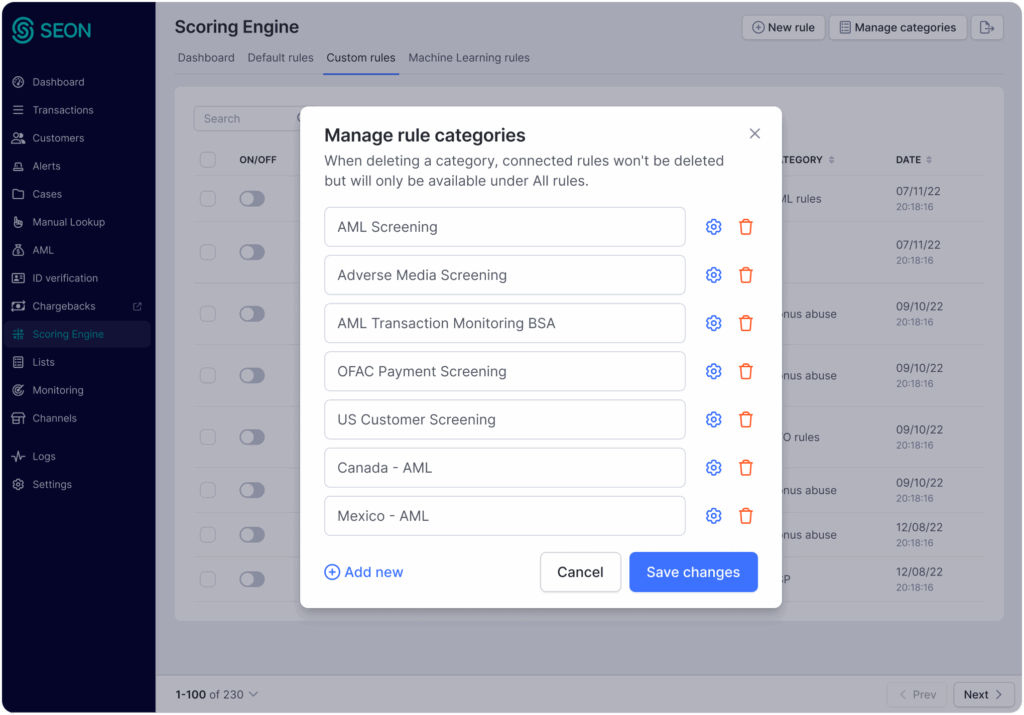
RULE CATEGORIES
Organize Rules by Product, Jurisdiction or Risk Type
Stop tracking rules in scattered spreadsheets. With rule categories, you can organize rules, giving investigators quick clarity on why a rule is flagged.
Deploy out-of-the-box rules for faster compliance
Launch your AML transaction monitoring program with pre-built rules from compliance experts or edit them to match your regulatory needs
Enrich detection accuracy
Use 900+ first-party fraud signals for smarter, context-aware transaction monitoring
See Connections From Every Angle
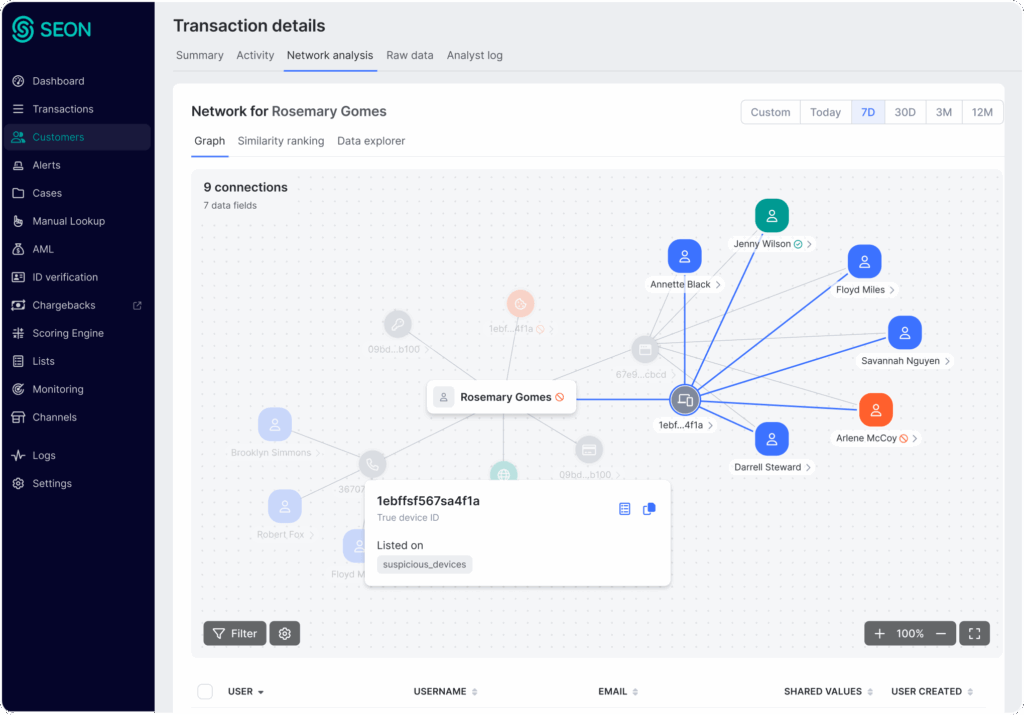
NETWORK GRAPH
Expose Hidden Connections with Graph-Powered Network Analysis
Every investigation is different. That’s why SEON lets analysts switch between ranked lists and an interactive network graph to explore connections, revealing the clearest insights for each case.
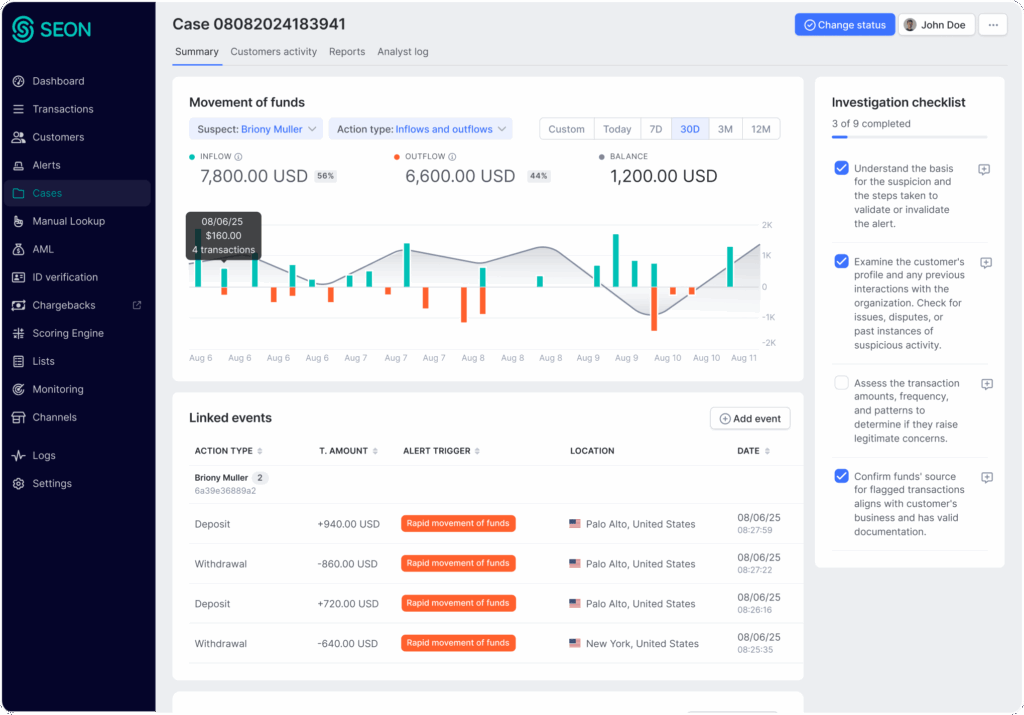
MOVEMENT OF FUNDS
Trace the Flow of Money to Spot Suspicious Patterns
See how funds move in and out of accounts by visualizing transaction activities to reveal layering or unusual patterns.
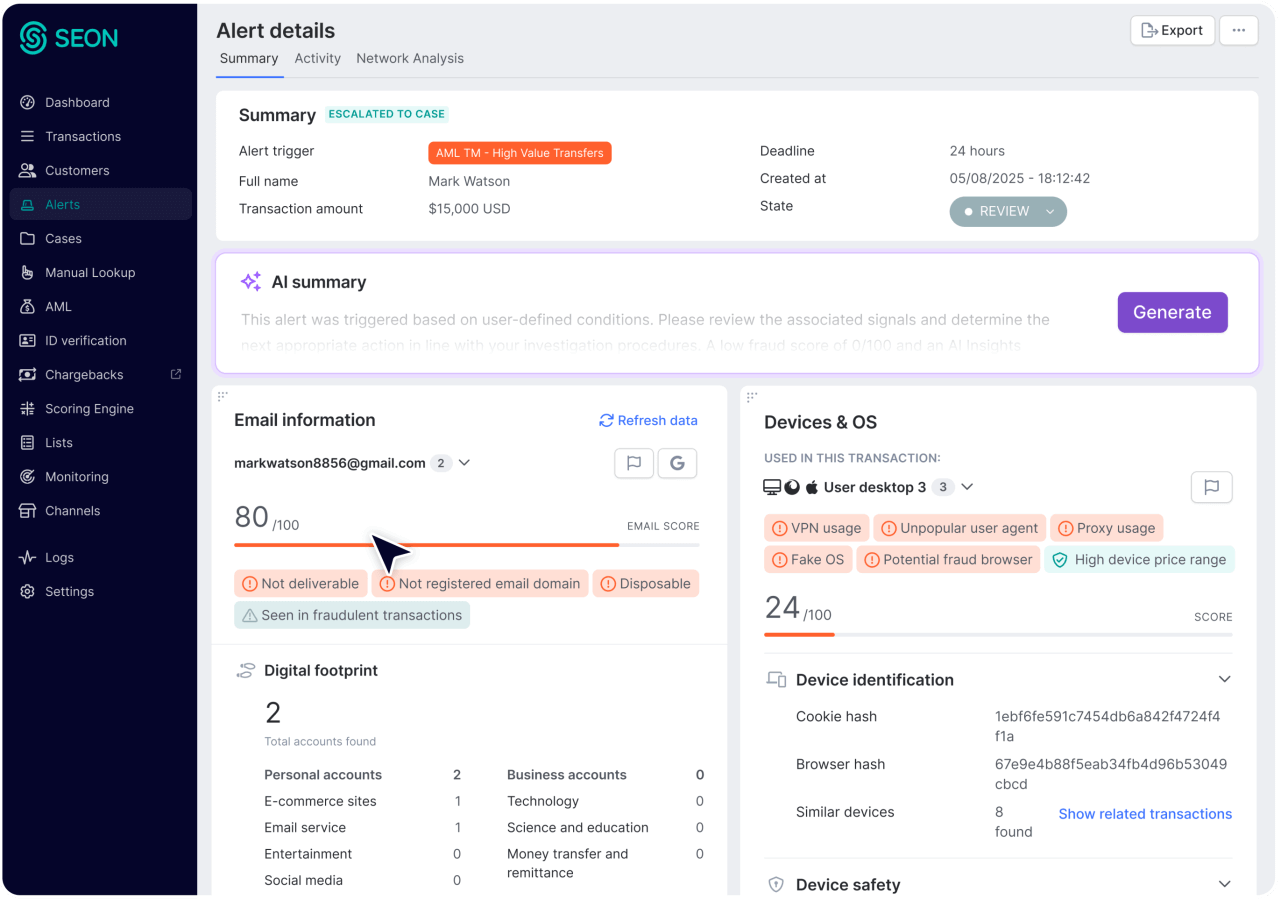
Turn Alerts Into Insight
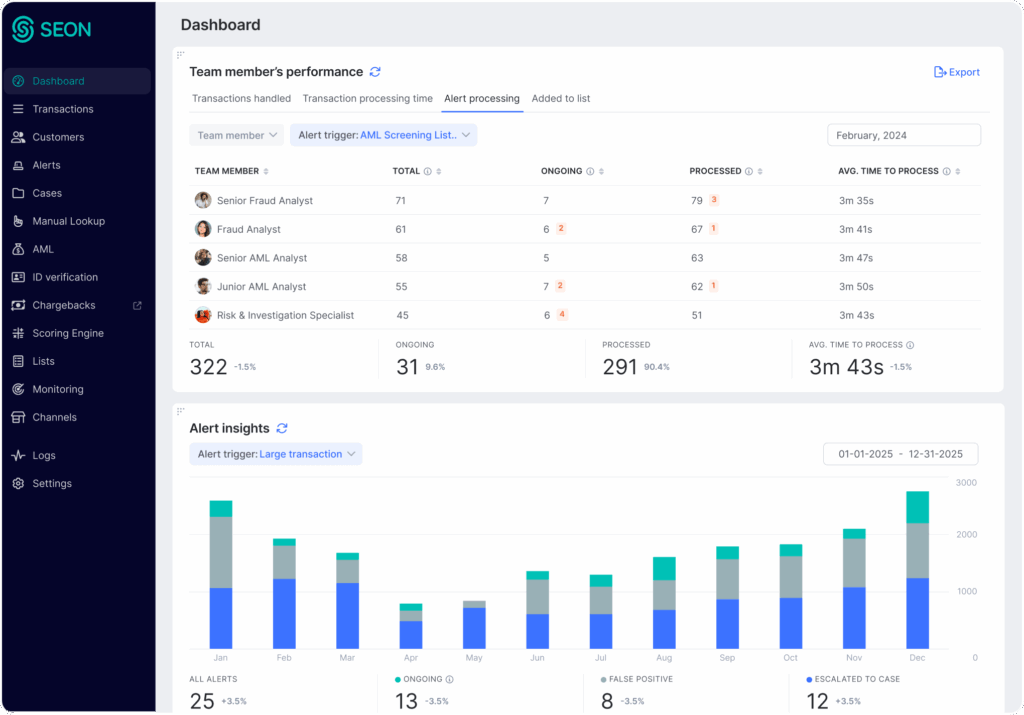
ALERT INSIGHTS & PROCESSING DASHBOARDS
Track Alert Volumes, Performance and Case Outcomes
Get instant insight into how alerts are handled across your team and down to each investigator. Track outcomes, manage workloads and boost decision quality with clear, actionable data.
MAKE YOUR COMMAND CENTER YOURS
Personalize Investigation Dashboards to Fit Your Workflow
Rearrange the alert, customer and transaction details pages to match your workflow. Each investigator can drag, drop and reorder each widget into their preferred layout without affecting anyone else’s view.