Business email compromise (BEC) attacks can be a major risk to businesses’ finances and reputations.
According to the FBI’s 2020 Internet Crime Report, 2020 alone saw 791,790 complaints of suspected internet crime – an increase of more than 300,000 since 2019. Reported losses in 2020 exceeded $4.2 billion. The report states that these victims mostly lost their money to BEC scams.
Thankfully, as BEC attacks are often a product of human error, many can be avoided with due diligence and training – both of which can be enhanced with the right fraud prevention tools.
Let’s look at what business email compromise attacks are and explore some of the many ways you can combat them.
What Is a Business Email Compromise Attack?
A BEC attack is when a fraudster gains unauthorized access to a business’s account. The most damaging form of BEC is account takeover (ATO) attacks. Fraudsters use manipulation tactics such as email-based phishing or take advantage of leaked company data to gain access to – and take over – one or more of the business’s accounts. BEC is also often carried out by a fraudster impersonating a member of the target organization, especially someone senior such as an executive.
In other cases, a senior staff member might be targeted through channels such as messenger services, phone calls, or via social media. One telltale sign that something is amiss is that such communications will always request sensitive information. It’s worth noting here that you can always act on your initial suspicions by running a quick email lookup against an address associated with a dubious message. Check out SEON’s address lookup widget below to see this approach in action.
[email_ip_phone_lookup]Business email compromise attacks are carried out in many ways, examples of which we’ll cover below. Despite its versatility, BEC invariably involves the misuse of compromised login credentials, with the aim of accessing sensitive information located in various business accounts (not just email inboxes – fraudsters also target intranet documents, HR records, and plenty of other sensitive archives).
One use case of BEC is when fraudsters use compromised data to trick staff into providing further information, such as their bank details or company secrets. Fraudsters may do this by impersonating the organization’s CEO (check out the CEO fraud section below to learn more about this).
Accordingly, BEC is not just limited to account takeovers and identity theft, but can also be a means for fraudsters to become imposters looking to subject the target company to further data breaches.
Main Examples of Business Email Compromise
BEC is wide-reaching because it’s accessible to many fraudsters and its purpose is broad: Fraudsters use it to exploit company infrastructures with stolen login credentials and account takeover attacks. As such, there are many examples of how BEC can be carried out. Let’s take a look at some of the key ones.
Email Data Breach Compromise
An email data breach compromise is simply an instance of sensitive information being leaked or stolen due to the use of either email-based phishing or email-based hacking, such as the use of a trojan horse or other malware infection.
While there are many methods and consequences of a business email compromise, an email data breach compromise occurring in a business is essentially the result of a successful BEC.
Vendor Email Compromise
A vendor email compromise (VEC) is when a fraudster focuses their BEC attack on a supplier, such as an online seller of office stationery. There are two main ways they can carry out a VEC: By impersonating the vendor or by impersonating the vendor’s customer or contact.
Such impersonations can be achieved by account takeover (ATO) or simply by the fraudster claiming to be the email contact through false credentials, such as a fake but convincing email address. This is often achieved with subtle character changes: Consider how much [email protected] looks like [email protected] to an unsuspecting reader, for example.
Tricks like this mean a fraudster can get away with asking the vendor’s customer to send such payments as “updated subscription fees”; or, on the other side of the fence, they can pretend to be a customer who “never received the products they paid for” and ask for a refund.
Discover SEON technology and how it can help any business make better decisions, boosting safety and growing without risks.
Ask an Expert
CEO Fraud
CEO fraud is a catch-all term for the exploitation of the account of a high-ranking organizational official, such as a CEO or an investor. This exploitation can be based on subjecting the official to an account takeover, such as by manipulating them into providing their account credentials; or, simply impersonating them as a means to commit a social engineering-focused phishing attack.
For instance, high-level staff who practice poor password hygiene – or have been tricked into providing their login details – are likely to be targeted, and they’re also likely to have sensitive information. Fraudsters look out for people who fit such a profile.
Knowing that more junior staff members will likely jump to give one of their senior bosses the information they request, some fraudsters make an email address that looks almost identical to the real official’s address and try their luck with demands for money, data, and so on.
How Does a BEC Affect Your Business?
Here are some of the major BEC pitfalls – namely the financial, reputational, and employee engagement issues – that may arise, alongside some associated statistics:
- Financial burdens: BEC attacks can be extremely costly. According to the FBI’s Internet Crime Complaint Center’s (IC3) Internet Crime Report 2022, the IC3 received 21,832 BEC complaints with adjusted losses of over $2.7 billion in 2022.
- Reputational damage: Concerns over a business’s reputation go hand in hand with its level of trust in new email contacts. It is telling that, according to IBM’s Cost of a Data Breach 2022 report, 41% of organizations had implemented the architecture known as Zero Trust into their operations. This means that a significant proportion of the surveyed businesses decided that traditional approaches to email security, such as firewalls, were not enough and should be enhanced with authentication processes such as multi-factor authentication (MFA) and encryption technologies.
- Reduction in employee engagement: Your staff’s time, progress, and concentration takes a significant hit when a costly BEC attack plagues your business. A GreatHorn report from 2021 states that 43% of surveyed organizations experienced a security incident in the 12 months prior to the survey – and 35% of them said that BEC and other phishing attacks accounted for over 50% of those threats.
While each and every organization will have different approaches and setbacks when faced with BEC attacks, the fact remains that business email compromise brings significant damages to the finances, trust, reputation, morale, and overall employee engagement of your business.
How to Prevent Business Email Compromise Attacks
BEC attacks can largely be carried out solely using social engineering attack-based phishing attempts. This means many instances of BEC can be prevented by mitigating human error through staff training. Alongside this, there is the need to use software best practices such as multi-factor authentication to reduce account takeover and other online impersonation attempts.
Here’s a closer look at the preventative measures:
- Maintain the best possible password hygiene, especially as many BEC attacks stem from users’ credential data leaks. One key solution is to make sure your work accounts and passwords are always different from your personal credentials, as fraudsters will likely try to log into your private accounts if they know your business credentials – and vice versa.
- Ensure both your staff and your software are equipped with the latest security best practices, such as the latest cyber-safety training and the use of email filtering and anti-spam applications.
- Use multi-factor authentication (MFA) to alert you immediately to an unrecognized sign-in attempt.
- Be wary of any emails requesting sensitive information, particularly from unrecognized contacts.
- Consider using a Zero Trust security architecture, as this ensures that any requests for a business’s online resources first go through an authentication and authorization process – regardless of whether the source of the request comes from inside or outside your organization.
It is important to remember that BEC attacks are like many other cyberattacks: The best way to prevent them is by making sure you’re safe online. Limiting human error with training and optimizing your equipment with the best software will reduce the chances of business email compromises considerably.
Solutions to Mitigate and Prevent Risks from BEC
The key is to ensure your business’s internal IT infrastructure is optimized to ensure the necessary checks and security measures are in place, especially if your organization uses a proprietary internal network. Maintain anti-virus software, as many BEC attacks trick email recipients into downloading malware – and always contact your email provider if you suspect or encounter a BEC attack.
The below infographic shows a seven-part, step-by-step approach that can, at best, enable your staff to prevent BEC attacks and, at worst, mitigate the effects of such attacks:
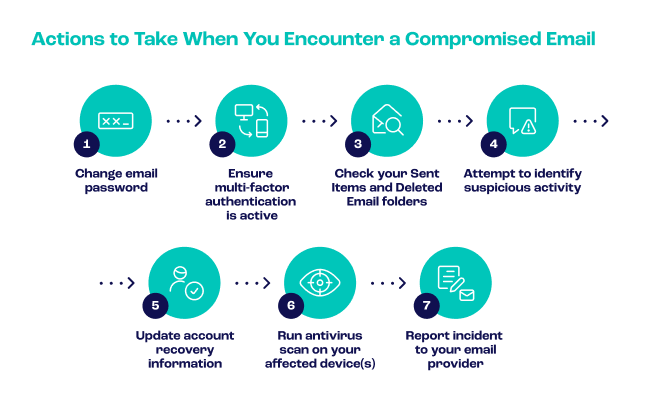
To elaborate, the first two steps are to ensure your email account activity is protected by the most basic security activities: Changing your email password and making sure your device is protected with MFA. To fend off your most recent attacker, this should be done immediately.
Afterwards, it is time to ask yourself how this could have happened in the first place. Checking your sent items and deleted folders will help you answer this question by showing that you or a co-worker have contacted suspicious contacts – or even overlooked threatening emails altogether by deleting them without reporting them. This is how you attempt to identify suspicious activity. Doing this will make a similar attack far less likely in the future.
Similarly to the importance of keeping your MFA use up to date, you will benefit from acknowledging an unfortunate truth: Aside from your work email account, your recovery email account may have been compromised as well. This is why you should also update your account recovery information.
Bear in mind that many people have more than one email address nowadays, such as their work and personal accounts. The best way to be safe online is to make sure you change the password to both. Password data breaches are common, and compromised email could lead to further intrusions, especially if the incident led to an account takeover (ATO).
The final two points won’t just help you combat business email compromise but are likely to help with other security-focused tasks too. By running an antivirus scan on your affected device(s) and reporting the incident to your email provider, all involved parties will be better informed about how best to protect you if the problem arises again.
Improve your risk management with SEON’s real time data enrichment tools
Ask an Expert
SEON’s Help Against Business Email Compromise Attacks
All SEON features are there to reduce your chances of encountering various forms of cyberattacks, including BEC attacks. The major ways SEON achieves this are through its user activity monitoring capabilities.
User account monitoring is the process of analyzing users’ actions (such as unusual login schedules) and behaviors (such as when users suddenly access features they don’t usually use). SEON’s user account monitoring helps identify potential signs of unauthorized access and other fraudulent behavior.
Meanwhile, SEON’s IP lookup tool allows users to enter an IP address that they wish to scrutinize. SEON will then quickly provide login information, such as location data, for you to gauge whether the account connected to the address appears to be legitimate.
Let’s take a closer look at some ways that SEON’s user activity monitoring and IP lookup capabilities can help combat BEC attacks:
- SEON helps you determine what constitutes unwanted activity and behavior, set rules against those issues, and have the software flag or block suspicious users accordingly. For example, if a user keeps logging in and out of an account in quick succession, they may be committing an ATO attack against one of your staff purely for the purpose of a BEC. SEON is able to log users’ account use and login history; unusual behaviors and timings will help you determine a user’s risk level.
- SEON’s IP lookup tool can identify dubious geolocation activity. For example, someone claiming to be from your organization – but who actually logged in from another country – can be spotted by SEON’s software and flagged for review.
SEON’s user activity monitoring and IP lookup capabilities combined help you determine whether certain users and email contacts should be treated with caution.
Sources
- FBI: IC3 Releases 2020 Internet Crime Report
- IBM: Cost of a Data Breach 2022
- IC3: Federal Bureau of Investigation Internet Crime Report 2022
- GreatHorn: New Report Explores State of Evolving Email Threats
Related Articles
User Activity Monitoring Explained: Examples, Legality, and Tips