What Is a BIN Attack?
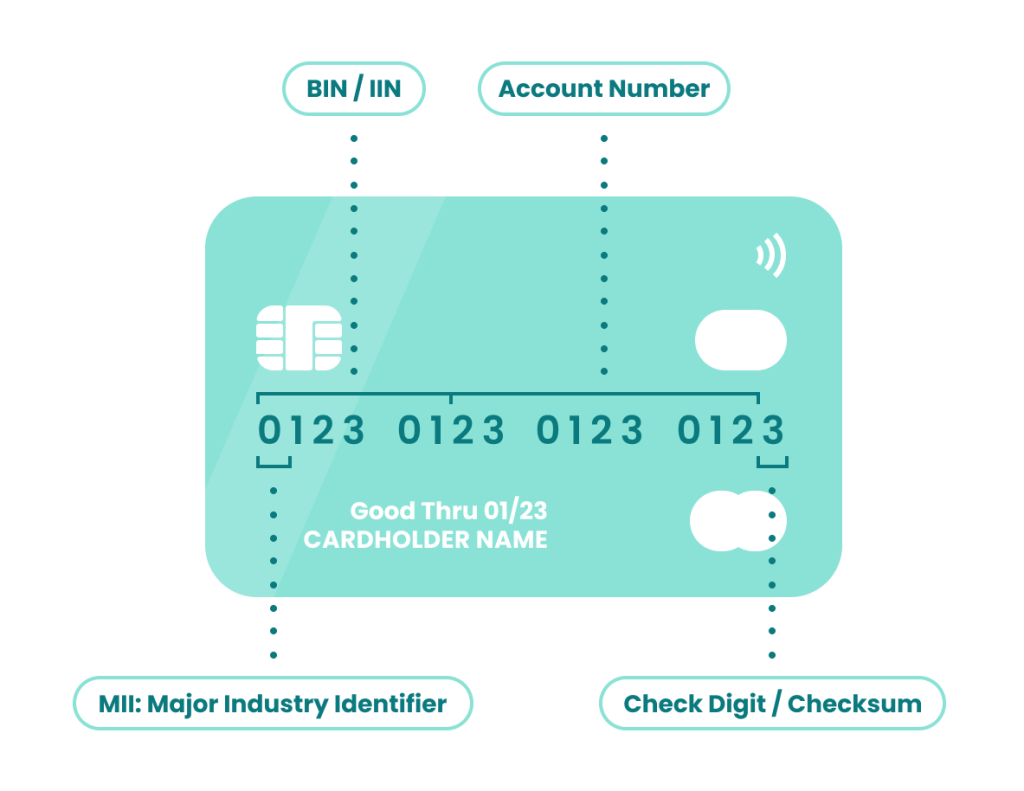
The BIN, or the Bank Identification Number, is the first six digits on a credit card. These are always tied to its issuing institution – usually a bank. In a BIN attack, fraudsters use these six numbers to algorithmically try to generate all the other legitimate numbers, in the hopes of generating a usable card number.
They then use them at various merchants to filter that list down to, essentially, whatever works. A brute force type of attack, it typically involves a large number of small transactions – as is typical in card testing.
These small transactions show up as various types of declines before they ultimately find any correct combinations – and potentially use them to discover even more. Because they only use card numbers, BIN attacks constitute card not present fraud.
How Does a BIN Attack Work?
Fraudsters conduct BIN attacks by generating hundreds of thousands of possible credit card numbers and testing them out.
- A fraudster looks up the BIN of the bank they will target. Ranging from four to six digits, this information is in the public domain and is thus easy to source.
- Using dedicated software such as an auto-dialer, they generate thousands, often tens of thousands, combinations of possible existing card numbers by this issuer.
- At this point, these credentials need to be tested. The fraudster identifies a suitable online shop or donation page.
- They start card testing by attempting a small payment with each generated card number.
- They keep track of the small percentage of card details that worked, which they are ready to use in earnest for their fraudulent pursuits.
Remember that the fraudster will start off with only six digits, yet there are many more card details required for a successful transaction. If those are entered erroneously, the transaction will decline.
This includes the CVV number, the expiration date, as well as likely address verification service (AVS) failures. Card testing transactions are executed remotely in a fast fashion, so distance checks should also be a hint as well as velocity alerts.
Fraudsters may use bad merchant accounts directly for this purpose, or more frequently involve multiple online stores and services during a BIN attack, as their attempts keep getting blocked at most outlets.
You can find information about a card and its issuer based on the BIN using SEON’s free tool below.
Who Does BIN Attack Fraud Target?
BIN attack frauds harm every single party that’s involved in a transaction, except the criminal. More specifically:
- Banking institutions: Successful BIN attacks can cost banks and other card issuers in funds, resources and reputation.
- Ecommerce merchants: Online shops and service providers also have a lot to lose from becoming the target of BIN attacks, including causing:
- Bank partnership issues as the bank identifies your store as one where cards are being tested and might choose not to work with you down the line.
- Reputational issues as the legitimate cardholder will see your shop’s name on their statement and associate it with fraud.
- Chargebacks: Depending on the particulars of the incident(s), you might have to pay the chargebacks out of pocket, instead of the card issuer.
- Payment gateways: Gateways involved in successful BIN attacks suffer reputational and possible financial damage, since they are expected to check various data points that would normally prevent BIN attacks from being successful. If you fail to catch such fairly rudimentary brute force attacks as a gateway, this is likely to be viewed by your partners and potential partners as evidence that you are not doing your job well.
- Customers: Any customer whose credit or debit card details are unfortunately involved in BIN attack fraud will have to first notice it and then spend time and effort informing the bank and going through the motions to get their money back. Contrary to some other types of fraud, such as card skimming, this is a type of attack which the cardholder has absolutely no control over, no matter how careful they are. As such, it can be even more frustrating.
How to Avoid BIN Attack Fraud
Depending on where you are in the payment landscape, a BIN attack will affect you differently.
Generally speaking, it’s a good idea to set up rules based on typical card testing behavior, including:
- setting up blocks for card issuer and GeoIP differences
- applying velocity checks on small transactions
- flagging multitudes of declines as high risk
Like in all card testing schemes, BIN attackers will look for small transactions that are quick to confirm and if you offer anything of that type as a merchant, you are at higher risk of being exposed to a BIN attack.
However, most anti-fraud rules and practices will cover BIN attacks in one way or another. And, in this type of fraud, even if the criminal has the correct card combination, they still won’t know the cardholder’s name or billing address, as well as several other frequently requested bits of information.
Yet, one should remember that with time, online fraud becomes ever more sophisticated; it’s rightly been described as a cat and mouse game between fraudsters and fraud-fighting specialists.
Even if BIN attack fraud in particular is fairly easy to catch, online merchants and everyone who might accept card-not-present payments are well-advised to implement appropriate levels of fraud detection and prevention.
Simply enter 6 to 8 digits on SEON’s lookup tool to perform a BIN lookup on any card and reveal information about customers’ true intentions.
Do a BIN Lookup