What Is 3-D Secure?
3-D Secure is a security layer protocol for online credit and debit card purchases. The name comes from the fact that three domains interact through it, with each kept “secure”:
- the merchant/acquirer domain
- the issuer domain
- the interoperability domain
The big card issuer companies offer the same 3-D Secure service under different names: Visa uses Verified by Visa/Visa Secure, Mastercard uses SecureCode, and American Express uses SafeKey.
Its general purpose is to make sure that the user making the purchase and the cardholder are one and the same, thus helping to prevent instances of fraud involving carding, card testing, chargeback fraud and so on. This is achieved through the use of a password that is only shared between the account holder and their card issuer (through an access control server), while the merchant only receives information on whether or not the check succeeded or failed.
In 2016, the protocol was updated by card issuers to be less intrusive and to be more understanding of contextual data: Now, trusted customers will not be asked to pass the check, which is only triggered for high-risk transactions.
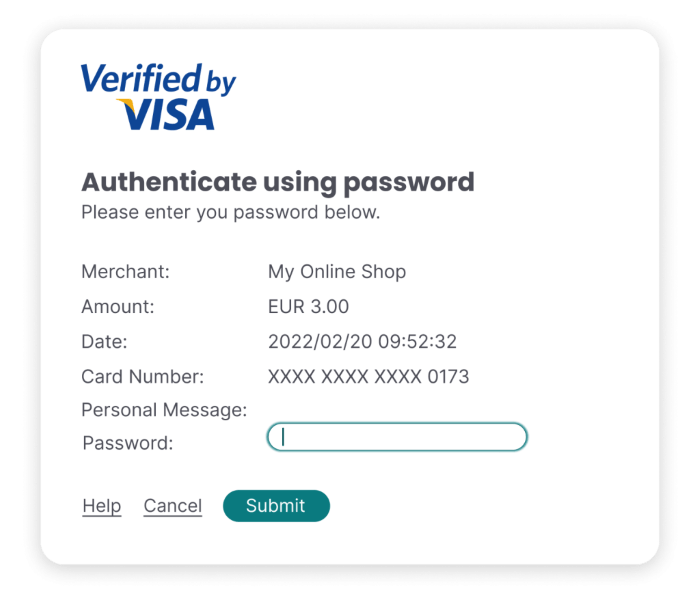
Typically, this check presents itself to the customer as an iframe or a pop-up window, where the user has to enter a code to complete the purchase. Theoretically, while card numbers are easy to acquire for criminals, this code is not and, as such, the liability in case of a chargeback shift from the merchant to the card issuer – except if the merchant has a high amount of fraud already and is being monitored.
How Does 3-D Secure Work?
- A buyer enters their card details (number, cardholder name, CVV)
- A popup window or inline frame is triggered, asking for a unique password
- The buyer enters their password, confirming they are the rightful cardholder
- The payment processor pushes the payment through.
The password is either set when issuing the card or more frequently it’s done by sending one-time passwords (OTPs) via SMS to confirm the cardholder’s intent. The process involves three players (or domains):
- Acquirer Domain: The merchant accepting the payment
- Issuer Domain: The company that issued the card being used
- Interoperability Domain: The infrastructure processing the payment and supporting 3-D Secure
Together, these three form the three Domains of 3-D Secure.
The protocol relies on XML messages sent over SSL with client authentication. A pop-up window or an inline iframe from the issuer side will present itself to the client, requiring a password that’s tied to the cardholder. It’s rare for the source of this to be the actual card issuer; it’s more frequently handled by the access control server – an outsourced third party handling 3-D Secure.
Why Is 3-D Secure Important?
While it comes at a cost to the merchant, this system significantly reduces the chances of unauthorized transactions and chargebacks. 3DS is deployed by default for certain high-risk markets or under certain card schemes.
However, from the user’s point of view, it’s an added friction to the buying process, especially when seen on the first occasion, and as such, it should be deployed sparingly.
3-D Secure was a protocol-level answer to the growing problem of credit card fraud. Contrary to common belief, an online transaction only needs a valid, active card number and expiration date to pass through. Even CVV codes are not mandatory.
As these became increasingly easy for criminals to acquire by copying, phishing or through hacked terminals, another security step was introduced: a shared secret between the issuer and the cardholder that’s not revealed to the merchant.
The reason for this is that the ecommerce merchant infrastructure is considered a weak link in case of a data breach, as opposed to the issuer or the client.
While early iterations of 3-D Secure drew criticism for being burdensome (in fact, the entire popup/iframe system was for a while being abused with phishing attempts), it is generally agreed to be secure enough for that trade-off.
The chance for an attacker to intercept the 3-D Secure code of the cardholder while making a transaction are slim, as they require the victim to be highly compromised, making 3DS an effective way of reducing unauthorized transactions.
How Does 3-D Secure Work with Fraud Detection?
In general, merchants apply 3-D Secure to high-risk transactions and enjoy the additional protection offered. Furthermore, the liability shift offered by 3-D Secure means that if the transaction is later disputed, the chargeback fees don’t apply to the merchant.
However, as it comes at a cost, both in terms of processing and in terms of user friction, one should be careful about how these security checks are implemented into the payment flow.
It is worth noting that in the European Economic Area (EEA), the PSD2 compliance requirements state that you are required to fulfill strong customer authentication (SCA) on purchases, which is effectively the same as 3DS2. 3DS1 will be discontinued from October 2022, and customer exemptions can be handled on your side via your risk tools to establish trust.
What Is the Difference Between 3DS2 and 3DS1?
The original 3DS1 was launched in 2001 by Visa, with improvements to it introduced in 2016, in the form of 3DS2.
Compared to 3-D Secure 1, 3-D Secure 2:
- involves considerably less user friction
- is only triggered for high-risk transactions
- is more understanding of contextual data
- can send more data to the bank than 3DS1
- recognizes soft declines
- supports exemptions
- statistically makes transactions less likely to be abandoned
With the new 3DS2, the payment process is much smoother, and a trusted user will glide through straight to a confirmation page or will be greeted with a familiar confirmation method – such as a fingerprint check or entering an OTP, whether in-app or in a browser.
Why Do 3-D Secure Authentication Failures Happen?
Not all 3-D Secure failures are a result of fraud.
Keep in mind that when triggered, this navigates the user to a different page, typically controlled by their issuing bank. Broadly speaking, there are three reasons for “legitimate” failure – which should be taken into account before you apply auto-blocks on further transaction attempts:
- The user had a problem receiving their one-time password or has misplaced their secure PIN. This is surprisingly common, especially for first-time online shoppers, as rare as they might be.
- The customer’s issuing bank does not in fact support 3-D Secure. This can happen if you force the check on every transaction in a given country, yet some banks still haven’t implemented it for a number of reasons.
- There is some sort of technical issue, like the access control service being down or something similar. This will also result in the check failing.
If, as a merchant, you have reason to think that the transaction might be legitimate despite a failed check, it is advised to get in contact with your customer asking them to contact their bank or to try again, explaining the issue.